Roughly 46% of hacked funds sit idle on-chain, suggesting alternatives for post-incident restoration, analysts at World Ledger say.
Hackers are fast, however the methods chasing them are nonetheless catching up. A brand new report by blockchain intelligence agency World Ledger, based mostly on lots of of on-chain incidents, reveals that in lots of instances, stolen funds land at laundering locations earlier than the hack is even publicly disclosed.
On common, it takes 43.83 hours from the preliminary on-chain breach till the incident is reported by both the sufferer venture or a third-party investigator, per the report shared with crypto.information. Hackers, in the meantime, have a tendency to maneuver stolen funds to the primary recognized entity, comparable to an alternate, a crypto mixer, or a decentralized finance protocol, inside 46.74 hours.
The longest delay, nevertheless, is the window between public disclosure and the attacker’s interplay with a laundering service, which averages 78.55 hours, suggesting that funds are sometimes already on the transfer nicely earlier than a hack turns into broadly recognized.
‘No clear playbook right here’
In complete, World Ledger’s researchers measured 4 key timelines throughout lots of of incidents. The time from breach to fund motion, from breach to reporting, from breach to first entity interplay, and from public disclosure to laundering exercise. Every lag additionally tells its personal story.
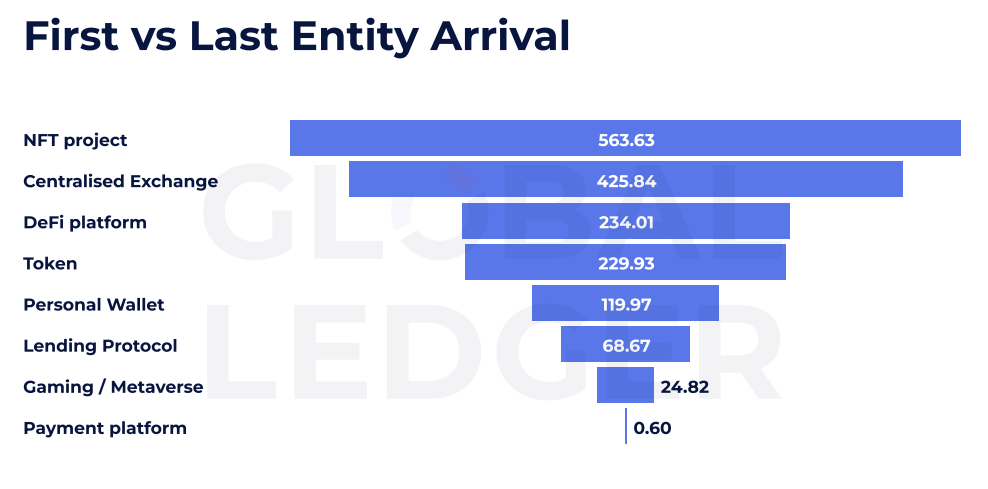
Assaults focusing on NFT initiatives, for instance, present the slowest fund actions. On common, it takes 563.63 hours — or almost 24 days — for funds from these exploits to maneuver from the primary to the final recognized entity within the laundering chain. That’s greater than double the typical lag seen in centralized exchange-related hacks, which clock in at round 425 hours.
World Ledger co-founder and CEO Lex Fisun instructed crypto.information in an unique commentary that the lengthy delay — in case of NFTs — isn’t nearly low liquidity as these tokens are “distinctive and more durable to dump quietly.”
“There’s no clear playbook right here, laundering often entails wash buying and selling or social engineering. Keep in mind The Idols exploit, the place the attacker drained $340,000 in stETH however acquired caught with the related NFTs.”
Lex Fisun
The report highlights how laundering paths range relying on the kind of venture exploited. DeFi platforms and tokens usually see funds transfer via laundering channels inside 230 hours, whereas cost platforms present the quickest turnaround: simply 0.6 hours on common. Gaming and metaverse exploits are additionally among the many faster flows, transferring in underneath 25 hours.
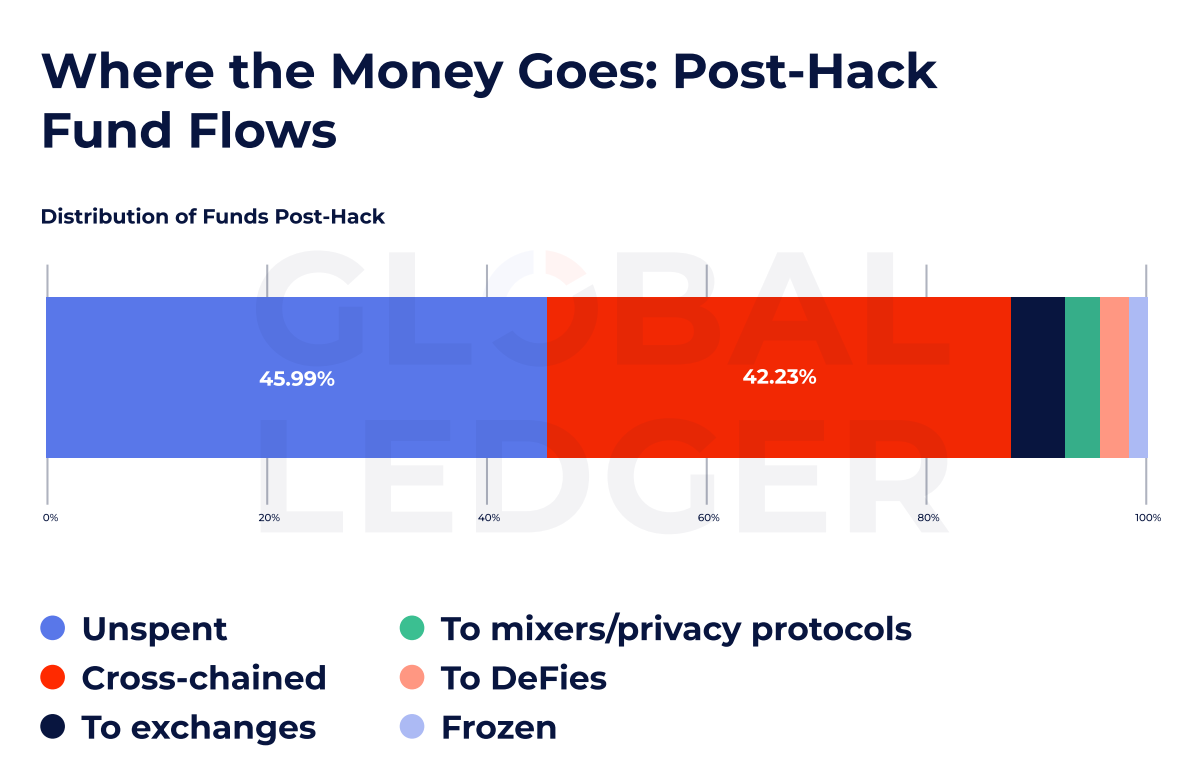
Regardless of the pace and fragmentation of fund flows, a stunning quantity of hacked property stay untouched. In line with the info, almost 46% of stolen funds are nonetheless unspent, suggesting important alternatives for ongoing monitoring and probably restoration, lengthy after an incident happens.
Cross-chain traces
Whereas many funds sit idle, a rising share is slipping via harder-to-trace cross-chain routes. The report reveals that 42.23% of stolen funds have been moved throughout chains, bypassing chain-specific monitoring methods.
Fisun defined that cross-chain bridges “have already turn into one of many prime cash laundering instruments” for slipping previous chain-specific monitoring. And whereas repeated abuse may draw AML scrutiny, the Twister Money case proves one factor: “sanctions shift ways, not demand,” Fisun added.
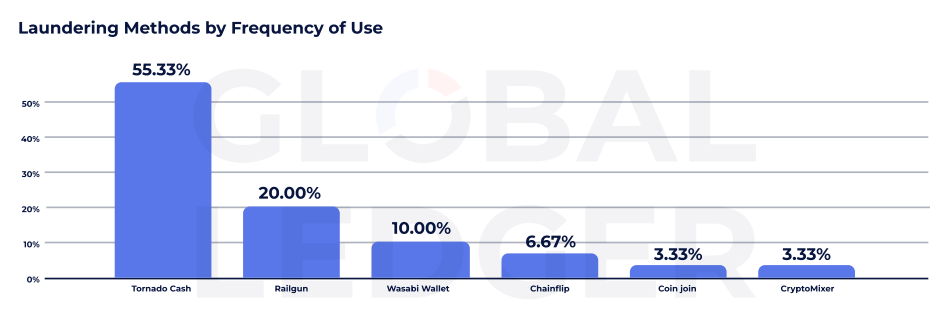
World Ledger’s information additionally reveals Twister Money stays the dominant laundering protocol, utilized in greater than 50% of instances tracked by the agency. Regardless of U.S. Treasury sanctions in 2022, and mounting stress from regulators globally, the service continues to play a central function in post-hack laundering.
Its use spiked once more after a U.S. courtroom ruling overturned the sanctions on constitutional grounds in 2024.
Different privateness instruments are additionally gaining momentum. Railgun, for example, was utilized in 20% of instances, whereas Wasabi Pockets appeared in 10%. Chainflip, CoinJoin, and CryptoMixer have been every concerned in lower than 7% of laundering flows, the info reveals.
Attackers getting smarter
Fisun famous that slower flows via centralized exchanges — now averaging greater than 425 hours — don’t essentially replicate higher compliance alone.
It’s each, the World Ledger CEO stated, including {that a} slower timeline “isn’t a glitch, it’s by design” as attackers break up property, hop chains, and use privateness protocols to maneuver stolen funds via CEXs that “attempt to delay flows that look shady.”
Solely a small portion of funds are frozen by enforcement or compliance groups. The report means that real-time responses stay uncommon, at the same time as analytics and monitoring instruments advance.
Whereas the numbers level to continued challenges, additionally they underline the place defenders can acquire an edge. The time gaps — generally measured in days — present that there’s nonetheless house to behave earlier than stolen funds totally disappear.